Description
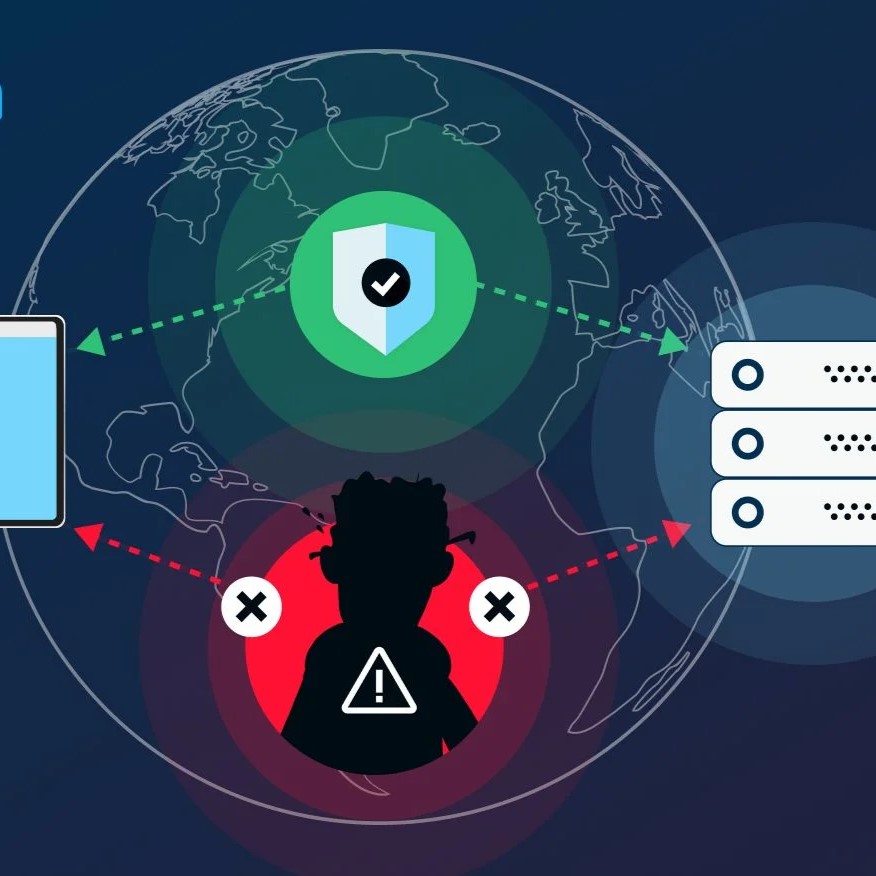
MitM attacks occur when an attacker secretly intercepts and alters communications between two parties, often on unsecured public Wi-Fi networks. Examples include eavesdropping, session hijacking, and SSL stripping. Protection methods include using VPNs, enabling HTTPS, and avoiding public Wi-Fi for sensitive transactions.





Olanrewaju –
I was having trouble with Man-in-the-Middle (MitM) Attacks, but this guide helped me understand the issue and provided step-by-step instructions to resolve it. The clear explanations and practical solutions made it easy for me to identify and fix the problem, ensuring that my network and devices remained secure. I found this guide to be extremely helpful and would recommend it to anyone experiencing similar issues.
Beauty –
This troubleshooting guide provided crucial insights and actionable steps to effectively identify and mitigate man-in-the-middle (MitM) attacks. Its comprehensive coverage of detection techniques and prevention strategies empowered me to safeguard my systems against malicious actors attempting to intercept and manipulate sensitive data. With clear instructions and practical examples, the guide enabled me to swiftly resolve MitM issues, ensuring the integrity and confidentiality of my online transactions and communications.