Description
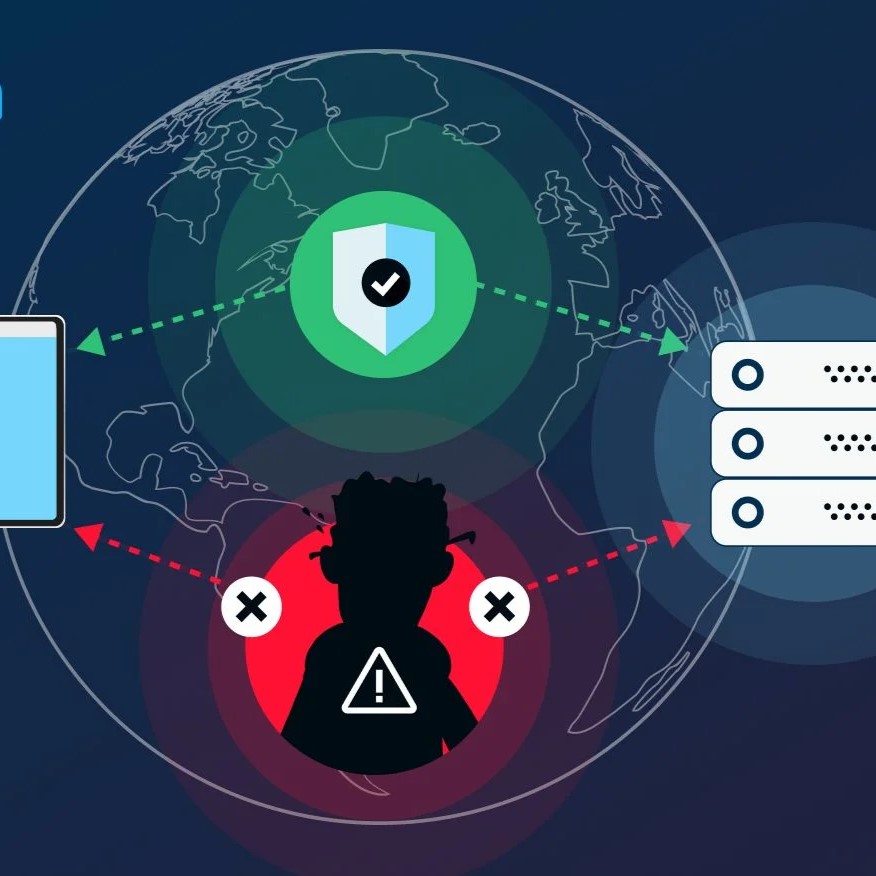
Phishing attacks involve deceptive emails, messages, or websites designed to steal sensitive information like usernames, passwords, and credit card details. Attackers often impersonate trusted entities such as banks or social media platforms. Spear phishing targets specific individuals, while whaling attacks high-profile executives. Users can protect themselves by verifying links, avoiding suspicious attachments, and using multi-factor authentication (MFA).






Olufunke –
This guide provides clear and comprehensive steps to identify and mitigate phishing attacks, empowering users to protect their sensitive information and online accounts. Its detailed descriptions, practical examples, and effective countermeasures offer invaluable assistance in safeguarding against malicious attempts to compromise security.
Alex –
The clear and concise structure of the Phishing Attacks Troubleshooting Guide made it easy to identify and resolve the issue quickly. The step-by-step instructions were detailed and accurate, guiding me through each phase of the solution efficiently. By following the guide, I was able to effectively combat the phishing attack and protect my data and systems with confidence.
Chris –
This guide provides comprehensive and effective solutions to the prevalent issue of phishing attacks. Its clear instructions and practical tips empower users to identify and mitigate phishing threats effectively. I particularly appreciate the in-depth analysis of various phishing techniques, allowing users to stay ahead of malicious actors. Overall, this guide has significantly enhanced my ability to protect against phishing attacks and maintain the security of my personal and professional information.